Platform Components
Analyst Console
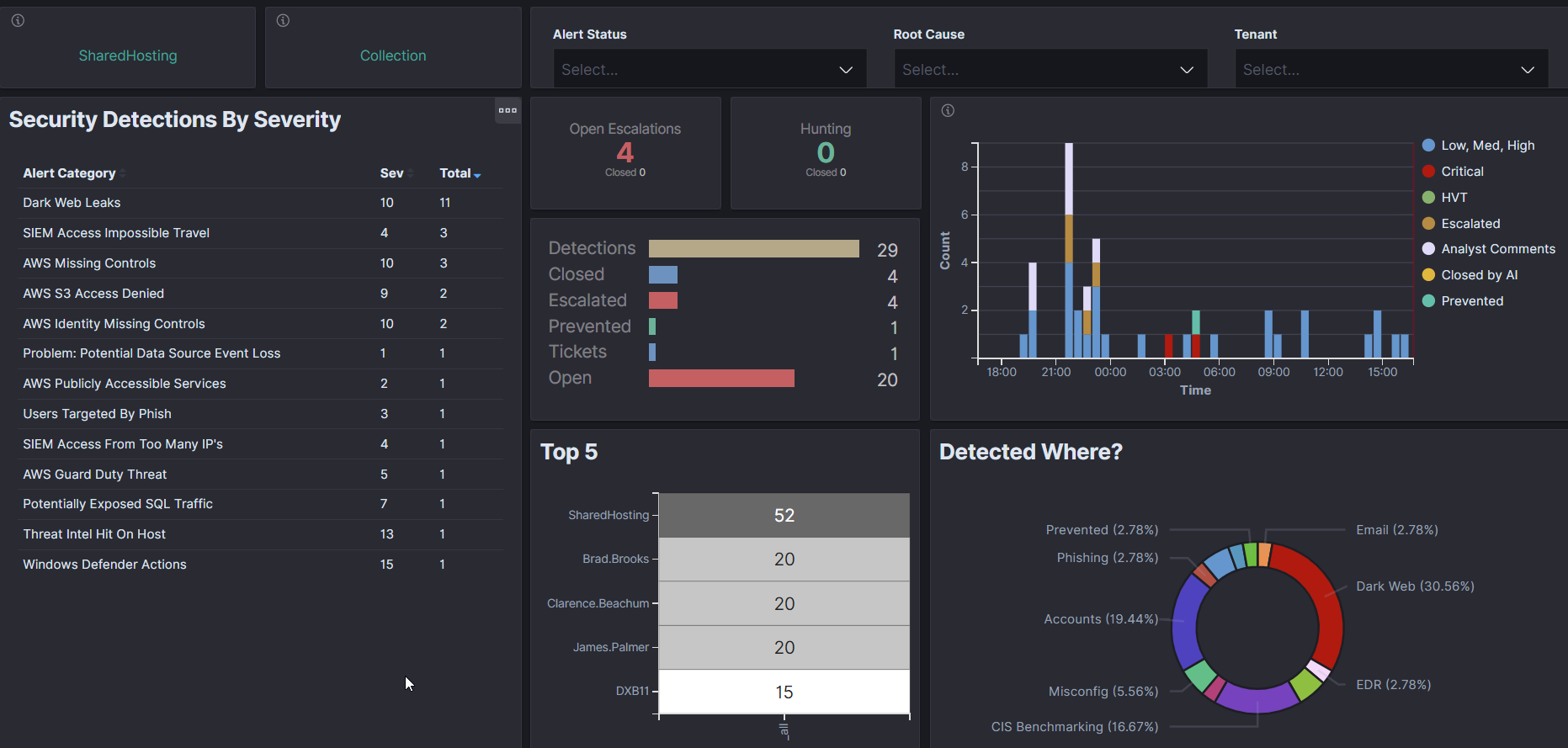
The Analyst Console is the main SIEM interface available to all eligible subscriptions. Tailored for security analysts, threat hunters, and incident responders, It provides access to your entire array of security event data and features a variety of dashboards and visualizations.
To access the console, simply navigate to https://console.threatdefence.io and log in with your email and password.
Here are some examples of the information available via the Analyst Console:
- Real-Time Threat Monitoring: Observe live data streams of security events across your network, enabling immediate identification and investigation of suspicious activities.
- Incident Management: Track and manage security alerts and incidents from detection through resolution. This includes the ability to assign incidents, document response actions, and close incidents upon resolution.
- Advanced Analytics: Utilize sophisticated analytics tools to dissect and analyze security events. This can aid in identifying trends, patterns, and anomalies within your security data, facilitating proactive threat hunting.
- Dashboards: Access dashboards that provide a detailed insights into your security events and posture. These dashboards can be tailored to highlight key metrics and data points relevant to your specific security concerns.
- Search and Investigation Tools: Employ powerful search capabilities and investigation tools to delve into historical security data. This enabled in-depth analysis of historical events and helps uncover the root cause of security breaches.
Related Articles:
Customer Portal
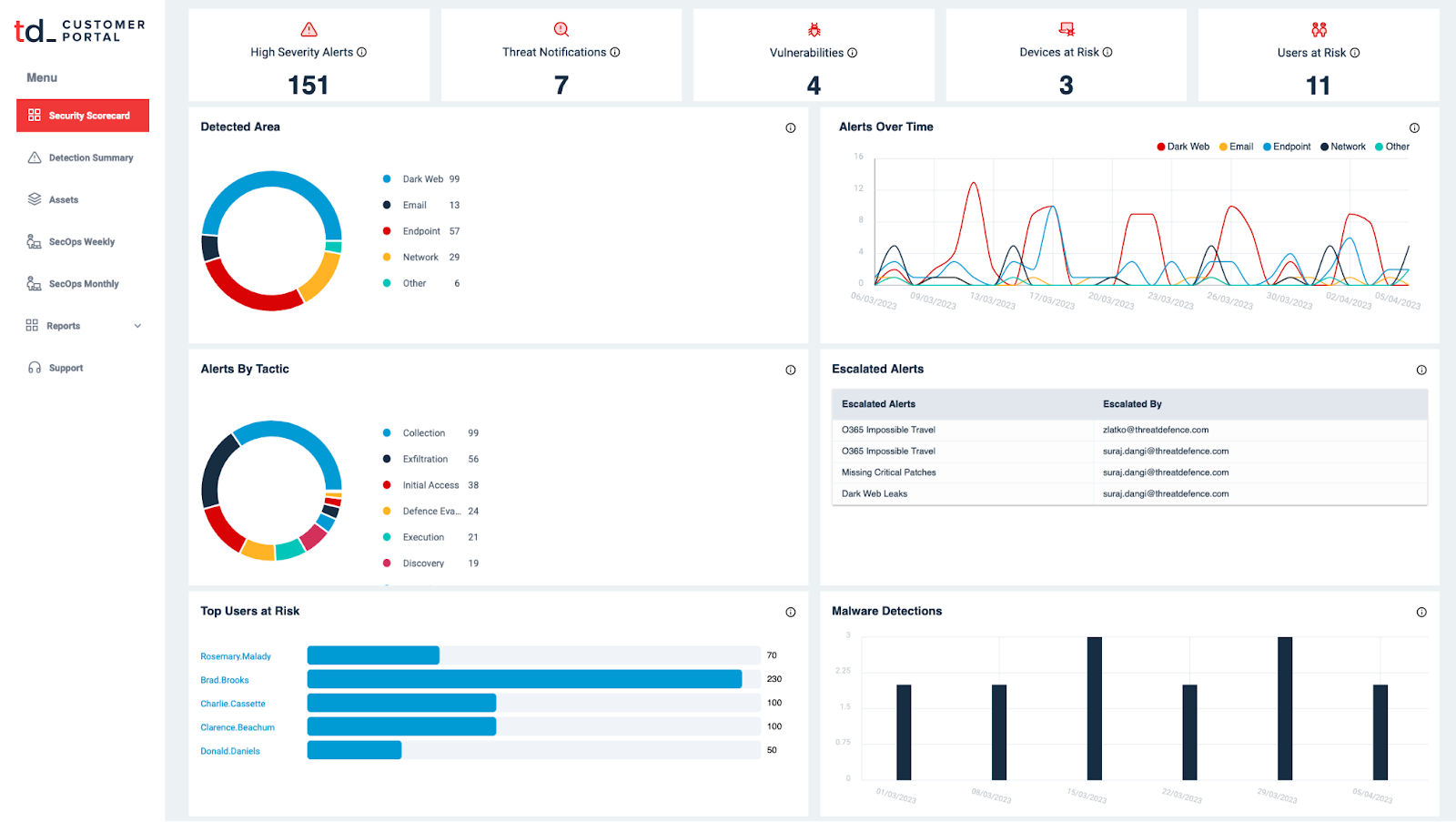
Our Customer portal is crafted to provide you with real-time and historical reports on your Security Operations, encompassing detections, actions executed by the SOC team, escalations, open security incidents, and threat notifications.
To access the portal, simply navigate to https://portal.threatdefence.io and log in with your email and password.
Here are some examples of the information available via the Customer Portal:
- Real-time Alerts: Immediate notifications about potential threats detected within your environment.
- Incident Reports: Detailed analyses of confirmed security incidents, including detected threats, affected systems, and remediation steps.
- SOC Team Activities: Logs of actions taken by the Security Operations Center team in response to detected threats and security incidents.
- Escalation Tracking: Information on the escalation process for high-severity incidents, including timelines and response strategies.
- Management Reports: Periodic reports detailing your organization's security posture and metrics.
Related Articles:
Endpoint Agent (TD Agent)
The endpoint agent is a single, lightweight agent that combines endpoint detection and response capabilities with our elite SecOps team, offering exceptional visibility and eliminating blind spots overlooked by traditional security tools.
The endpoint agent introduces unparalleled visibility capabilities, along with comprehensive security inventory functionality to enrich the security data gathered from our sources and unveil the most elusive actions carried out by the most sophisticated threat actors.
The latest version of the endpoint agent as well as deployment instructions are available on your portal at: https://portal.threatdefence.io/deployment/endpoint-agent
Related Articles:
Microsoft Entra ID / 365 Monitoring
As part of our SecOps product suite we support Microsoft 365 monitoring capability.
A major benefit is its compatibility across all Microsoft licensing tiers - we do not require premium P1/P2 licenses as a prerequisite for our solution to work.
Our platform offers comprehensive monitoring of user login sessions, activities on SharePoint and OneDrive, as well as Exchange Online events, among others. This allows for a detailed oversight of user interactions and system changes within the 365 environment.
Furthermore, we have incorporated a suite of predefined use cases and correlations designed to streamline the threat detection process within the MS 365 suite. This feature simplifies identifying potential security issues, making it easier for organizations to maintain a secure and efficient operational posture.
Related Articles:
- Onboarding M365
- Checking M365 User Activity
- M365 Alerts
Network Sensor (TD Network)
ThreatDefence network sensor (TD Network) is a real-time Network Detection and Response(NDR) solution which can be deployed to monitor inline network traffic on-premises or in-cloud, inspecting both horizontal and vertical traffic flows. The NDR detects even the most concealed activities and utilizes our machine learning technology to identify unknown threats, lateral movement and malicious insider behavior.
TD Network brings automated and integrated threat intelligence and expert human security-analyst threat hunting to your network to provide superior threat detection and response capabilities, leaving no threat undetected.
The collected data is transitioned to our SecOps platform and correlated with other information collected from endpoints, applications, system logs, and public cloud instances. Within our rich threat intelligence ecosystem, threat indicators are transformed into the full attack kill chain and all attack stages as seen in various parts of the environment are identified. TD Network brings full forensic investigation capability into your environment and supports full packet capture for advanced investigation and evidence collection.
Related Articles:
- Network Sensors
- NDR sensor - Virtual Platform Requirements
- Deploying a virtual NDR sensor - HyperV
- Threat Hunting with NDR
API Integrations (TD API)
ThreatDefence SecOps Platform simplifies the complex task of managing security threats from various tools by integrating seamlessly with a wide range of external systems. Our platform is designed to ingest security events data and threat detections from third-party tools, making it a central hub for your Security Operations. We support Antivirus, Endpoint Detection and Response (EDR) systems, email and web security gateways, and more.
By leveraging API integrations, ThreatDefence streamlines the process of gathering and analyzing security data from various sources. This approach not only enhances the efficiency of security operations but also significantly improves the ability to detect and respond to sophisticated cyber threats.
Some examples of popular API integrations include AWS, Azure EventHub, CrowdStrike, Microsoft Defender and SentinelOne.
Related Articles:
Syslog Integrations (TD Syslog)
We also support ingestion of standard syslog logs (firewalls, etc.)
All you need to do is set up a small virtual sensor within your environment. The sensor can aggregate syslog logs from multiple sources, and ship them to us is a secure and reliable way. The same sensor can be used to gather logs from multiple devices, or even from different customers or deployments.
Related Articles:
Additional Functionality
Depending on the size and complexity of your setup, we might activate some extra integrated tools to enhance your security operations and provide deeper insights. Here are some additional capabilities we might use:
- Honeypots: These are decoy systems designed to lure cyber attackers, helping us identify and analyze potential threats.
- Attack Surface Management: Keeping an eye on all the possible points where an attacker could try to enter your system, ensuring nothing is overlooked.
- Dark Web Monitoring: We monitor the Dark Web for any stolen data or threats against your company, keeping you one step ahead of cyber criminals.